EBL Bluetooth Unit
INNOVATIVE SYSTEMS
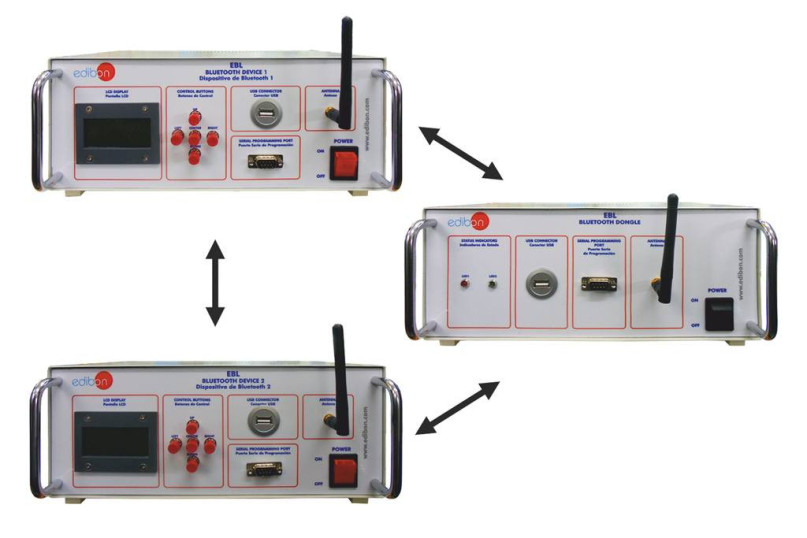
The Bluetooth Unit "EBL" is a complete unit to study a Bluetooth communication network between two autonomous devices and a computer through a Bluetooth Dongle.
Laboratories
RELATED NEWS
General Description
The Bluetooth Unit, "EBL", operates in conjunction with a computer, which is connected with the Bluetooth Dongle, that allows communicating and programming the Bluetooth Devices to perform a simple Bluetooth network.
The two Bluetooth Devices (included in the supply) have a LCD display that shows the current state of the devices (linking status, input messages, output messages, etc).
The "EBL" allows to perform a complete Bluetooth link between the computer and the Bluetooth Devices and to get familiar with all the procedure involved in the configuration of a Bluetooth link (configuring the link, scanning new devices, configuring the communication parameters, programming the Bluetooth Devices, encrypting the communication, etc).
This Computer Controlled Unit is supplied with the EDIBON Computer Control System (SCADA), and includes: The unit itself + a Control Interface Box + a Data Acquisition Board + Computer Control, Data Acquisition and Data Management Software Packages, for controlling the process and all parameters involved in the process.
Exercises and guided practices
GUIDED PRACTICAL EXERCISES INCLUDED IN THE MANUAL
- Familiarization with the trainer.
- Study of the different Bluetooth profiles.
- Establish a connection between master and slave devices.
- Analysis of the received signal strength indicator (RSSI) of a Bluetooth low energy (BLE) connection.
- Analysis of the writing and reading of a character in a Bluetooth communication.
- Familiarization with Bluetooth low energy packet sniffer.
- Use the Bluetooth low energy packet sniffer to analyze the advertising and discovery events.
- Use the Bluetooth low energy packet sniffer to analyze the start and termination of a link.
- Use the Bluetooth low energy packet sniffer to analyze the reading and writing of a character between devices.
- Familiarization with Bluetooth control software.
- Establish a connection between the computer and two Bluetooth slaves.
- Configure the connection parameters of a Bluetooth communication.
- Read and Write characters from an established Bluetooth network.
- Protect the Low Energy Bluetooth communication from MITM (Man in the middle) attacks by encrypting the connection with a passcode.
SIMILAR UNITS AVAILABLE
Computer Controlled GSM Communications Unit
SUPPLEMENTARY EQUIPMENT
Telephony Systems Unit
Computer Controlled GSM Communications Unit
Computer Controlled Satellites Unit
Radar Unit
GPS Unit
Lan Network Unit
Quality

AFTER-SALES SERVICE

 Cookie preferences
Cookie preferences